
Cyber Detectives
Step into the role of a cyber sleuth in Cyber Detectives, the nation’s first interactive exhibit designed to help visitors learn about internet safety.




Training Zone

Cryptobabel
Explore techniques for decoding secret messages.

Netbuilder
Use servers, routers and firewalls to build a network — and a high score.

Social Engineering
Learn to identify phony websites and phishing scams.

Hashing and Cracking
Is your password easy to crack? Hash it and find out!

Cyber Forensics
Isolate suspicious data and take measures to protect the network.
Creative Coding
Experience the “Internet of Things” by writing code to get a ball through a maze.

Passwords and Picking
Learn about password protection as you manipulate huge locks with removable pins.
Cryptography
Use multiple techniques to encrypt and decrypt secret messages.
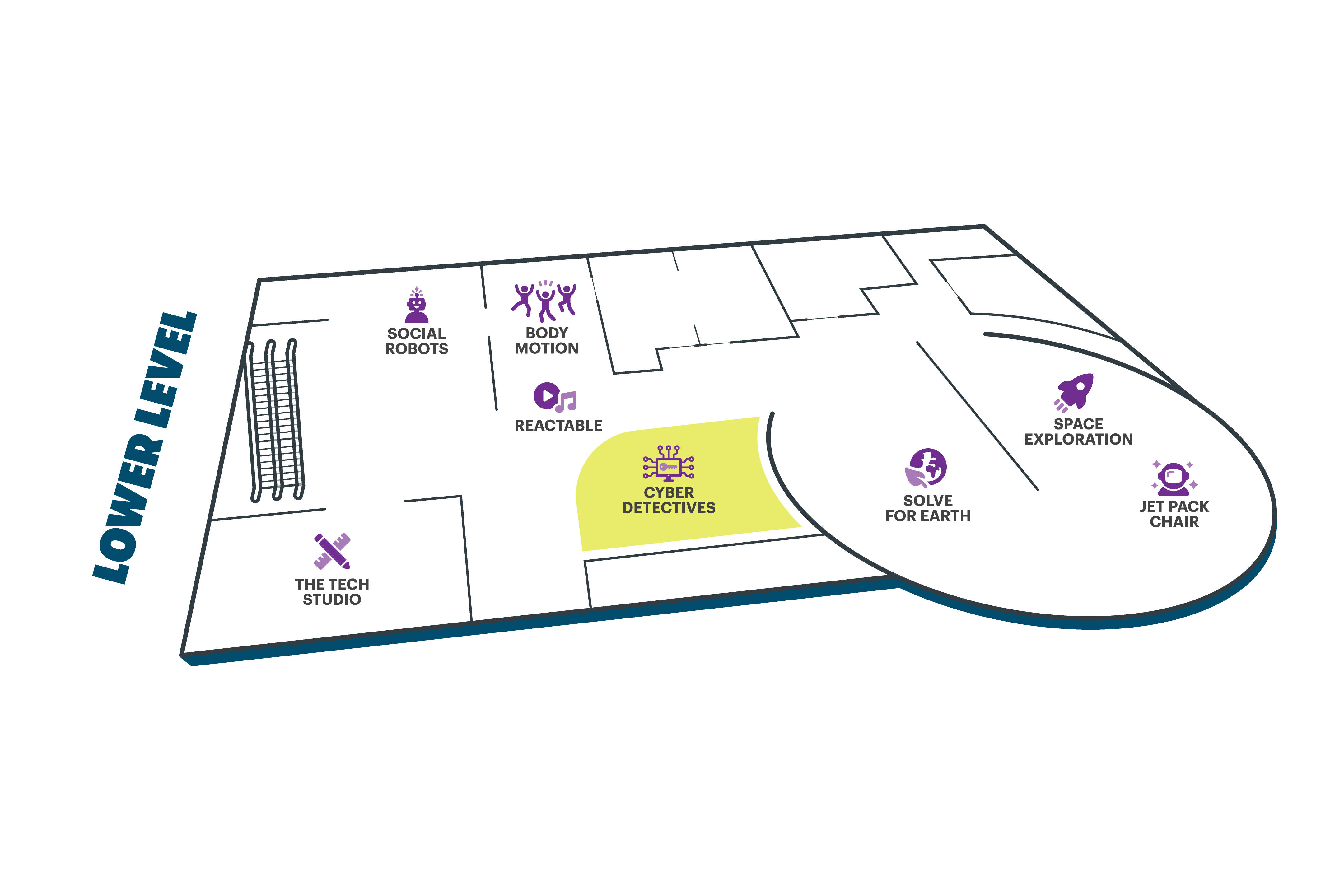
Location
Cyber Detectives is located on the Lower Level next to The Tech Studio and Solve for Earth.
Why is internet safety so important? Because the internet evolves constantly. So does crime associated with online activity and data security. We are each responsible for protecting our own digital lives, and Cyber Detectives will empower you to do just that.
Hone your skills in our training zone. Then enter our mission zone to test your knowledge as a cyber security professional in a full-fledged game. This exhibit is recommended for ages 12 and up.
And be sure to check out our innovative, standards-based lesson plans tied to each of these exhibits.
Mission Zone (Temporarily closed)
After you’ve completed your training, it’s time to test your skills in the “offices” of Acme Recycling, where you’ll step into the role of a cyber security professional.
Malware attacks and failing networks, data theft and financial breaches: Mayhem and chaos ensue as Acme’s network and personnel face a variety of cyber assaults. Four interactive missions will put your new skills to the test.

Cyber Espionage
A criminal has hacked into an employee’s computer. Crack her password so you can gain access, then identify and remove the malware while gathering clues about the culprit.

Cyber Sabotage
Acme’s recycling robots are out of control! Investigate network traffic and foil a spoofing attack, then create a blocking rule on Acme’s firewall that will reestablish control of the robots.

Social Engineering
Top-secret Acme data has been leaked (and an employee’s social media site isn’t helping). Establish a remote connection to help fend off a Trojan horse virus and a spear-phishing attack.

Financial Breach
Acme’s banking credentials have been stolen, thanks to an employee who fell victim to social engineering and was careless with a photo. Use clues to find the login credentials, crack the criminal’s password and take back control.
Exploring Ethics and Cyber Security
The Tech Interactive has partnered with the Markkula Center for Applied Ethics at Santa Clara University to help people identify and respond to the ethical questions presented by technology. Learn more:
- Ethical Questions about Encryption
- The Ethics of Online Privacy Protection
- Surreptitious Surveillance on the Internet: An Ethics Case Study
- Keys Under Doormats: Mandating insecurity by requiring government access to all data and communications (Computer Science and Artificial Intelligence Laboratory Technical Report)
- Hacker Lexicon: What are White Hat, Gray Hat and Black Hat Hackers?
- Face-Off: Is Vulnerability Research Ethical?
- Ethics of Hacking Back: A Policy Paper on Cyber Security
 Skip Navigation
Skip Navigation

